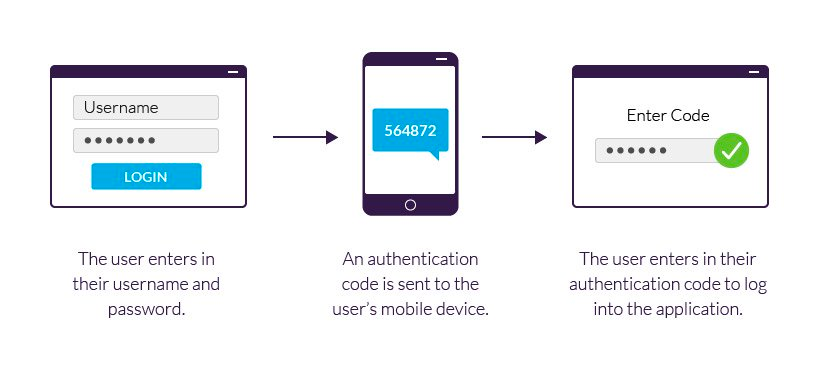
We recently added two-factor authentication (2FA) to Throne. 2FA is a great way to add an extra layer of security to an application's authentication system since it means that, even if a user's login credentials are compromised, the malicious party cannot log into the creator's account unless it can also verify it is in possession of the second factor needed for login.
This article will dissect the different options we looked at with respect to designing our 2FA system and will discuss the pros and cons of the final solution we built.
Possible Solutions
Self-built
One solution we initially designed was to build the 2FA system ourselves. This would give us maximum flexibility. It would mean that we would be able to flexibly add and remove 2FA options. We would use an external provider like Twilio for sending SMS messages and save the authentication codes to our database.
However, it would also mean that we had to a.) design the entire system and work with external providers (e.g. Twilio for SMS) to make it work, and b.) we'd have to vet, secure and debug any system we built.
Firebase

The second option was to use Firebase's prebuilt 2FA system. This system supports SMS 2FA out of the box. Firebase has a quick and easy guide on how developers can add this functionality to their app. You also need to upgrade your Firebase billing instance and pay a little more, however, this is definitely worth it.
Using this guide any developer can easily and quickly add 2FA to their application, using Firebase's SDK.
Evaluation
Pro: Quick
We were able to build 2FA in as little as two weeks, from start to deployment to production. As a startup with constrained resources, being able to quickly ship code that works reliably is a big upside.
Pro: Seamless
We experience very few bugs and can be confident in the system's ongoing performance. Furthermore, it is directly integrated into Firebase's authentication flow and so the UX is very streamlined. We do not need to worry about edge cases or weird in-between states, Firebase does this for us.
Con: Only works for password authentication
Firebase 2FA only works for email + password authentication. This is annoying but not a fundamental problem. The other supported login methods are Google, YouTube, Twitter and Twitch, each of which support 2FA on their own platforms. As such, if a user wants to secure their Throne login with 2Fa if they are using Google Login, then they need to add 2FA to their Google Account.
Con: Limited number of 2FA options
The biggest limitation we found with Firebase's 2FA system is that it only supports SMS verification. Whilst being better than nothing, we would preferably support further verification system such as email 2FA, OTP 2FA (with Google Authenticator) and security keys.
Conclusion and Next Steps
Overall, integration 2FA with Firebase was an efficient process. It works reliably and can be taken off the shelf. We would definitely use Firebase 2FA again, if we were to go back in time.
However, we continue to improve the system. We have added a ticket adding further 2FA options to our product backlog and will be adding this functionality very soon.
If you have any questions about authentication, 2FA or Throne in general, feel free to contact us at support@jointhrone.com.